- Blocks internet connection
- Block exe files from running
- Installs itself without permissions
- Connects to the internet without permission
- Normal system programs crash immediatelly
- Slow internet connection
- System crashes
- Annoying Pop-up's
- Slow Computer
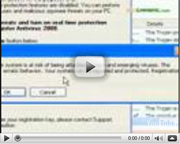
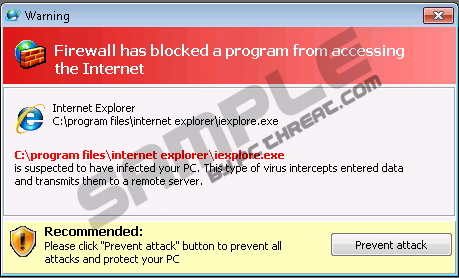
Windows Processes AcceleratorIf you get suspicious alarm messages from Windows Processes Accelerator, keep in mind that you confronted with a fake security application which is waiting for you to lose your resistance to fake security threats. This malware was created to persuade you to waste money on removal of simulated infections. What we are trying to do is to persuade you to get rid of this Windows Processes Accelerator as it has no reason to be left in your system. The system might catch Windows Processes Accelerator through bundled downloads, fake online scans or attachments from suspicious senders. It may also get onto the computer via Trojans while you are secretly trying to “study” pornographic websites. Thus, however the system got infected, it will be loaded with fake pop-up messages, very brief simulated scans or even with slight system slow downs which might not be noticed at all. Now that we overviewed the main features of this rogue, do not forget to kick it off your computer. The disposal of Windows Processes Accelerator is not that nice and easy unless you know how to get rid of the rogue without system’s damage because manual deletion requires you to be a skilful IT technician. If you can remove Windows Processes Accelerator manually, you may stop reading here, but if you are still wondering how to root this pest out of the system, get a legitimate antispyware tool which will automatically scan the system, detect Windows Processes Accelerator and remove it from the system. UPDATEFurther research into the subject has revealed that Windows Processes Accelerator is nothing else but a direct clone of Windows Care Taker, Windows Custodian Utility, Windows Shielding Utility and many other rogues from the Rogue.VirusDoctor family. They copy the appearance of legitimate operating system's interface, and as a result make user think that things like Windows Processes Accelerator is a legitimate program as well. Unfortunately, there is nothing beneficial about Windows Processes Accelerator and you are advised to "register" it with this registration code: 0W000-000B0-00T00-E0020 You simply need to click the "Activate Ultimate Protection" button and enter the code into the rogue's registration window. Afterwards Windows Processes Accelerator will behave as though you have really purchased the license. It will stop displaying these fake security messages: Error Warning! Identity theft attempt Detected System Security Warning Windows Processes Accelerator will also tell you that all of the infections have been removed and it will unblock your system tools such as Windows Task Manager or Registry Editor. You will also be able to use the Internet again, but you cannot let your guard down just yet. The rogue is only sedated but it will come any time, so in the meantime you have to acquire a powerful computer security tool that will erase Windows Processes Accelerator from your computer in no time. Do all it takes to terminate Windows Processes Accelerator and remove it from your system for good.
Download Spyware Removal Tool to Remove* Windows Processes Accelerator
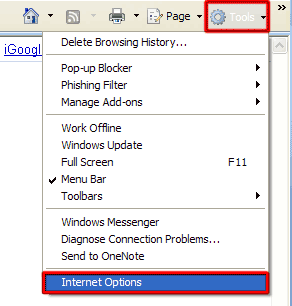
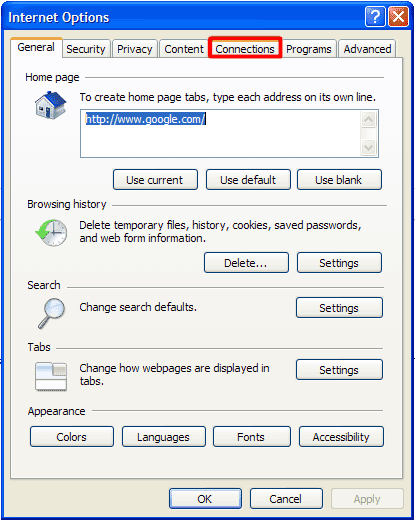
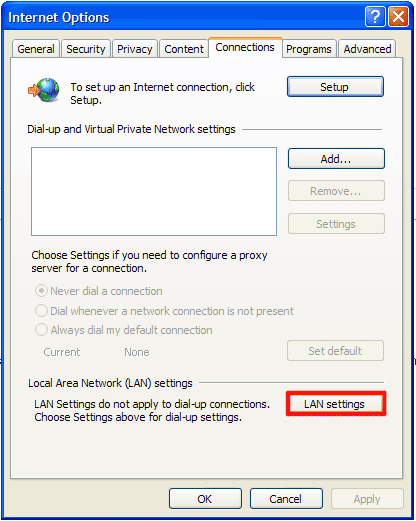
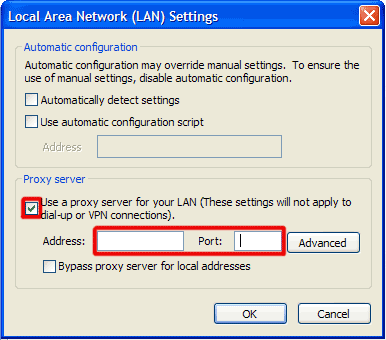
How to renew your internet connection:This rogue antispyware blocks your Internet connection to prevent you from removing the rogue application. To enable the Internet connection, please follow these instructions:
| ||||||||
|
Download Spyware Removal Tool to Remove*
Windows Processes Accelerator
| ||||||||

|
How to manually remove Windows Processes Accelerator
Files associated with Windows Processes Accelerator infection:
%CommonStartMenu%\Programs\Windows Processes Accelerator.lnk
%AppData%\result.db
%AppData%\Protector-[Random].exe
%AppData%\NPSWF32.dll
Windows Processes Accelerator DLL's to remove:
Windows Processes Accelerator processes to kill:
Remove Windows Processes Accelerator registry entries:
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Settings "UID" = "okanrqfdwk"
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\atro55en.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\bisp.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\esafe.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\install[4].exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\mssmmc32.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\pcip10117_0.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\scrscan.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\utp

Post comment — WE NEED YOUR OPINION!