- Blocks internet connection
- Block exe files from running
- Installs itself without permissions
- Connects to the internet without permission
- Slow internet connection
- System crashes
- Slow Computer
- Annoying Pop-up's
- Normal system programs crash immediatelly
Windows First-Class ProtectorDid Windows First-Class Protector start performing a scan of your computer? Well, in that case, you can be sure that you are infected with a rogue anti-spyware. You might have downloaded it accidentally with an online scanner, or it might have been installed in your system by the sneaky Trojans. Just like its clones Windows Trouble Taker or Windows Debug Center, Windows First-Class Protector is difficult to notice and tricky to remove. Windows First-Class Protector has one purpose: it tries to steal your money and credit card data and it does that persuasively by shocking you with a bunch of threats it detects every time this rogue scans your computer. Nonetheless, do not ever trust what Windows First-Class Protector says, for it only pretends to be a real security tool when, in reality, it is nothing but a hoax! You must ignore all the notifications it tries to scare you with and delete Windows First-Class Protector, because it does not protect you from real infections that might contaminate your system and even cause inoperable computer. However, you can protect your system from Windows First-Class Protector by updating your operating system and fixing all the loopholes through which this rogue can sneak in easily. Furthermore, you need to have a reliable security tool remove Windows First-Class Protector from your system and use it to protect your system from future infections. Finally, you should make sure that you have your firewall fully functioning, surf the Internet carefully and avoid potentially dangerous websites, especially the ones containing pornographic content. UPDATEAs it has been established already that Windows First-Class Protector is a part of the Rogue.VirusDoctor family, you have an upper-hand in this battle against the dangerous rogue antispyware. That is to say - you know what to expect from Windows First-Class Protector, and how to remove it. First of all, you need to know how to discern between the real system messages and the fake messages sent by Windows First-Class Protector. The main difference is that Windows First-Class Protector's messages urge you to purchase the full version of the program. Here are a few examples of the said messages: Warning Warning! Identity theft attempt Detected Error Then you have to stay calm and do not do anything rash when Windows First-Class Protector blocks your Internet browser and Windows Task Manager. It will certainly do so, because it is the best way for the rogue to protect itself at the same time making it seem as if other infections are responsible for the erratic computer behavior. If you want to bypass Windows First-Class Protector's defenses, you should use this registration key: 0W000-000B0-00T00-E0020 Register Windows First-Class Protector with this key, and it will stop the rogue from sending fake security messages, and unblock the system tools you need to remove Windows First-Class Protector. Now, you can try deleting the rogue on your own, but judging from the files related to the rogue (such as Protector-yblo.exe), Windows First-Class Protector comes to your system with a bunch of Trojan infections, and removing a Trojan on your own might be a rather tedious task. Save yourself the trouble of dealing with multiple infections manually by investing in a trustworthy computer safeguard tool, which will terminate Windows First-Class Protector for you in no time, along with the other infections present.
Download Spyware Removal Tool to Remove* Windows First-Class Protector
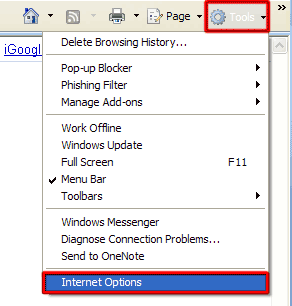
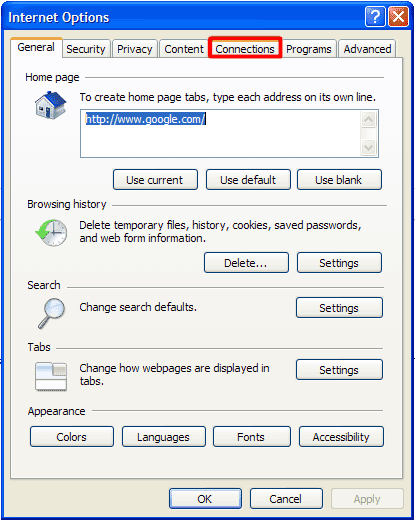
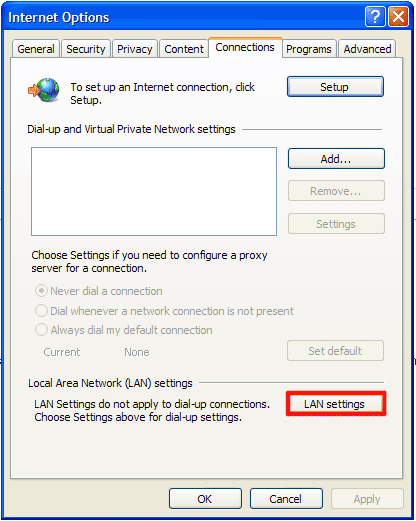
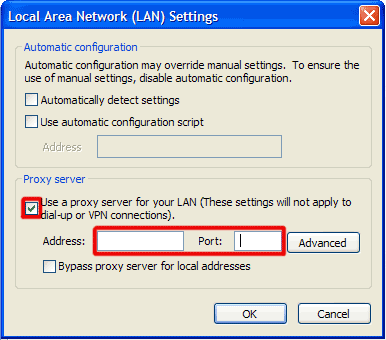
How to renew your internet connection:This rogue antispyware blocks your Internet connection to prevent you from removing the rogue application. To enable the Internet connection, please follow these instructions:
| ||||||||
|
Download Spyware Removal Tool to Remove*
Windows First-Class Protector
| ||||||||

|
How to manually remove Windows First-Class Protector
Files associated with Windows First-Class Protector infection:
Protector-yblo.exe
%AppData%\NPSWF32.dll
%AppData%\Protector-[Random].exe
%AppData%\result.db
%Desktop%\Windows First-Class Protector.lnk
%CommonStartMenu%\Programs\Windows First-Class Protector.lnk
Windows First-Class Protector DLL's to remove:
Windows First-Class Protector processes to kill:
%AppData%\Protector-[Random].exe
Remove Windows First-Class Protector registry entries:
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Settings "UID" = "okanrqfdwk"
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\atro55en.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\bisp.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\esafe.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\install[4].exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\mssmmc32.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\pcip10117_0.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\scrscan.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\utpost.exe

Post comment — WE NEED YOUR OPINION!