Executioner RansomwareIf your PC has been infected with Executioner Ransomware, then beware that it was encrypted many of your files and you need the appropriate decryption key to decrypt them. The problem is that the ransom payment may be too high or you may not receive the key once you have paid. Therefore, we recommend that you remove this malware from your PC, but note that once you have deleted it, you will not be able to decrypt your files using the decryption key you bought. Therefore, protecting your PC from malware such as this is very important as neglecting its security can bring undesirable consequences. Once on your computer, Executioner Ransomware is set to enumerate all of the files on your Pc and then start encrypting them with a unique RSA-2048 encryption algorithm. This algorithm has a 2048 Bit key size, and it provides this ransomware’s developers with a very strong and secure encryption that cannot be cracked that easily, if at all. While encrypting your files, this ransomware will append them with a custom extension in addition to the original extension. For example, your file may be appended with a randomly generated extension such as “.wax8kq,” “.yxzs2z,” “.uwcbhi,” “.orrwdy.” These extensions are just a few possible combinations. They indicate that a file has been encrypted, but changing the extension or editing it in any way will not decrypt the file. Once the encryption is complete, Executioner Ransomware will drop a ransom note named Sifre_Coz_Talimat.html on the desktop and in each folder where a file has been encrypted. Furthermore, it will also change the desktop image featuring similar information to that in the ransomware note file. This ransomware’s developers want you to pay 150 USD in Bitcoins, and you are required to send the payment to 164eQzsZUZCR9mfLWGdiqqGcUyQsYcX6vU — the cyber criminals’ Bitcoin wallet address. Once you have made the payment, you are expected to email your unique ID number found in Sifre_Coz_Talimat.html to executioner.update@protonmail.com and wait for the decryption key. If you delete this ransomware prior to decrypting your files, then you will be unable to decrypt them at all. The decryption key along with the decryption software should be sent to you within in 24 hours. However, you should not expect it to be on time or receive it at all. We have found that Executioner Ransomware is part of the Hidden-Tear ransomware family as its source code is the same as that of Resurrection Ransomware, Decryption Assistant Ransomware, Korean Ransomware, and several others. Its secretive developers release a new ransomware every once in a while to earn some cash. However, malware developers were quick to pick up on this new ransomware, so programs such as SpyHunter are already detecting and eradicating this new ransomware. Given the extensive damage this program can do to your personal files, you should try to avoid getting it in the first place. If your PC has not been infected with Executioner Ransomware, then you should know that its developers have made arrangements to have it send in malicious emails. These emails are sent to random email addresses and may not look out of the ordinary. The emails can be disguised as receipts, invoices, and so on. Furthermore, the ransomware can look like a PDF file while being and EXE file in fact. Hence you need to check whether a file has a double extension to see whether it is a fake file. The text inside the malicious email will point you to opening the attached file, and this file is the ransomware. The file can be dropped into the %TEMP% folder if you open it without downloading. However, if you downloaded it first, then check the folder where you directed it to be downloaded to and get rid of it. We advocate for the removal of Executioner Ransomware because its developers might not keep their word and send you the decryption key. You can use the deletion guide below or get an anti-malware program such as SpyHunter to get rid of it for you. Removal Instructions
Download Spyware Removal Tool to Remove* Executioner Ransomware
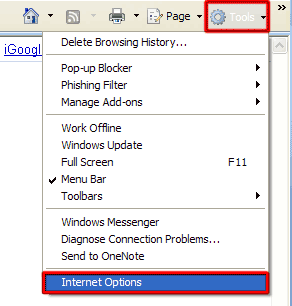
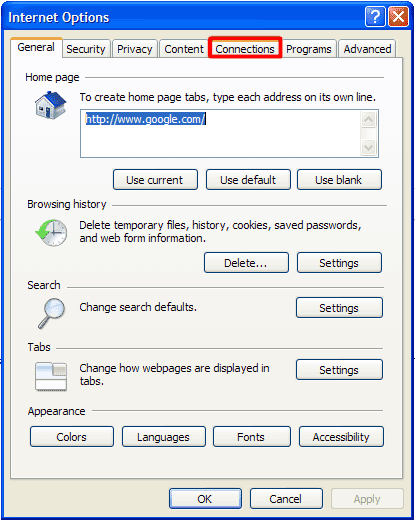
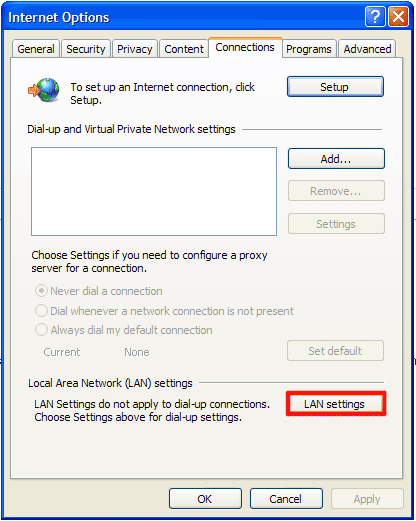
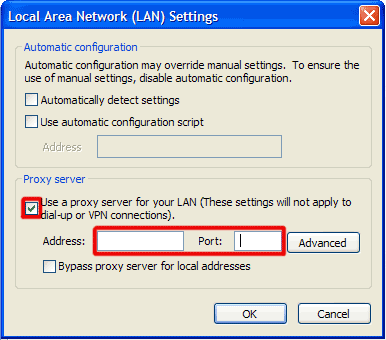
How to renew your internet connection:This rogue antispyware blocks your Internet connection to prevent you from removing the rogue application. To enable the Internet connection, please follow these instructions:
|
|
Download Spyware Removal Tool to Remove*
Executioner Ransomware
|

|

Post comment — WE NEED YOUR OPINION!