- Blocks internet connection
- Block exe files from running
- Installs itself without permissions
- Connects to the internet without permission
- Shows commercial adverts
- Slow internet connection
- System crashes
- Annoying Pop-up's
- Slow Computer
Windows Web CommanderTrojans, encrypted downloads, social engineering scams, spam emails, and various other security backdoors have been implemented to spread Windows Web Commander virus throughout Windows systems all around the globe. The rogue’s interface replicates the blue/red color scheme and layout of such Windows programs as Windows Security Center, which is one of the main elements that helped the fictitious application to have fooled hundreds of unsuspecting Windows users with its fake removal tool. The rogue, which has been developed and distributed by tremendously clever and knowledgeable cyber criminals – creators of the clone Windows Interactive Security, – can block your Internet connection, running of most executable files, and can even remove administrative privileges to access Registry Editor and Task Manager tools, which could be used to trace and delete Windows Web Commander from your computer. You can remove these symptoms by using a special registration number, which will fool the rogue into believing that you have paid for its full version. Registration number: By all means, you should not spend a dime on this fictitious application’s licensed version, because this way you would risk your personal data and identity security to be breached by extremely devious cyber crooks. To remain protected against the cunning Windows Web Commander virus scam, make sure you ignore all type of malware detection reports and security notifications, all of which will be completely fake, and all of which serve a sole purpose of making you believe the alleged infection: Error Error Recommended: Warning! Spambot detected! If you are not familiar with malware removal tasks, manual Windows Web Commander removal is not recommended for you, because you could easily delete legitimate Windows components, compromising your system even further. For this reason, using automatic removal tools would be the best idea, and your system could benefit from this option most, because it would be ensured a reliable, full-time protection against malware, which could easily attack your PC, if it is not guarded by strong software.
Download Spyware Removal Tool to Remove* Windows Web Commander
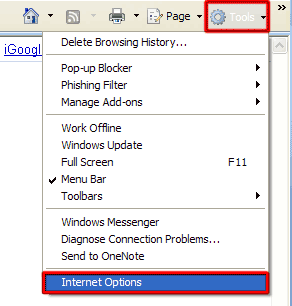
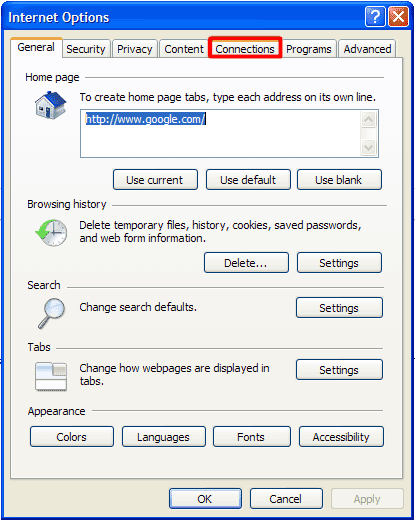
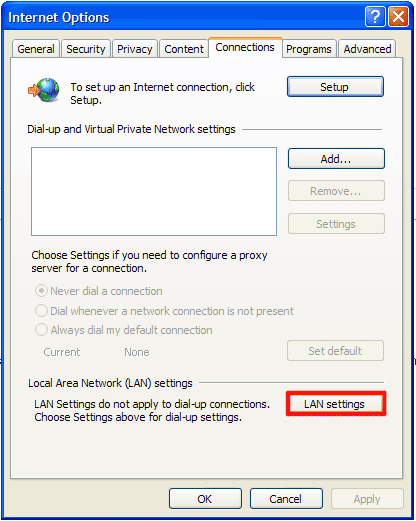
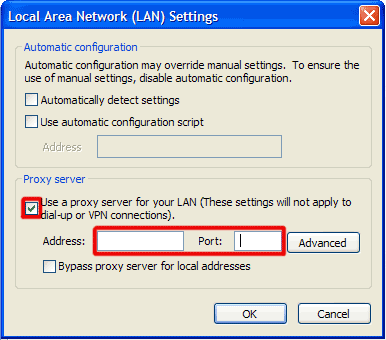
How to renew your internet connection:This rogue antispyware blocks your Internet connection to prevent you from removing the rogue application. To enable the Internet connection, please follow these instructions:
| ||||||||
|
Download Spyware Removal Tool to Remove*
Windows Web Commander
| ||||||||

|
How to manually remove Windows Web Commander
Files associated with Windows Web Commander infection:
%CommonStartMenu%\Programs\Windows Web Commander.lnk
%AppData%\1st$0l3th1s.cnf
%AppData%\result.db
%AppData%\Protector-[Random].exe
%AppData%\NPSWF32.dll
Windows Web Commander DLL's to remove:
Windows Web Commander processes to kill:
Remove Windows Web Commander registry entries:
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Settings "UID" = "otbpxlqhjd"
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\alevir.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\cmdagent.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\install[1].exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\npfmessenger.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\protector.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\srng.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\tsadbot.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\xp_antispyware.exe

Post comment — WE NEED YOUR OPINION!