- Block exe files from running
- Installs itself without permissions
- Connects to the internet without permission
- Shows commercial adverts
- Slow internet connection
- System crashes
- Annoying Pop-up's
- Slow Computer
Windows Ultimate Security PatchWindows Ultimate Security Patch is an identical clone of Windows Defence Counsel, and both of these fake antispywares belong to the Rogue.VirusDoctor family. We can assure you that if this tool’s computer scanner is running without any of your authorization, you should remove it at once, as it is a highly dangerous cyber criminals’ production, which will be used to extract your money in the most treacherous and sinister way. So, if various security notifications (see bellow) are already misleading you with recommendations to remove non-existent malware, install security tools, which will remove Windows Ultimate Security Patch from your PC for good. Warning! Spambot detected! Recommended: Error Error If these fake notifications do not convince you with application’s malicious intentions, understand that Windows Ultimate Security Patch is also responsible for removed access to Registry Editor and Task Manager, blocked Internet, and disabled ability to launch some executable files. Even though this may seem as an outcome of dangerous viruses, Trojans and other malicious programs, it is just an implementation, which is employed by cyber criminals to make it impossible to detect and remove Windows Ultimate Security Patch from Windows right away. If you believed that these symptoms were the result of malicious activity of fictitious infections, it would be much easier for the rogue to trick you into purchasing antispyware’s full version removal tool. This is something you should avoid by all means! Since Windows Ultimate Security Patch is terribly hazardous to your personal safety, it would best that you deleted it at once, either manually or automatically. Manual removal option is the more complicated one, and demands great knowledge and malware removal skills, so if you do not think that could can manage successful operation, your best option is to download antimalware software, which would delete Windows Ultimate Security Patch in minutes. To be able to connect to the Internet, you should either use connection renewal guide bellow, or apply a license key, which would restore full Windows functionality. License key:
Download Spyware Removal Tool to Remove* Windows Ultimate Security Patch
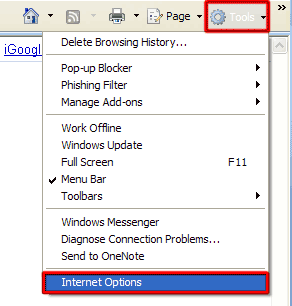
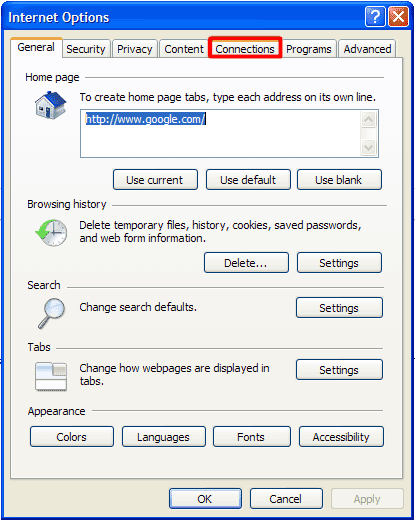
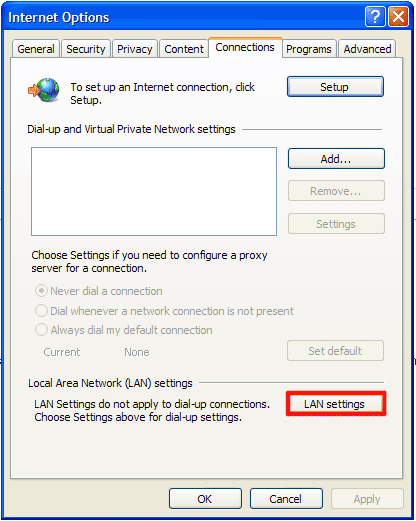
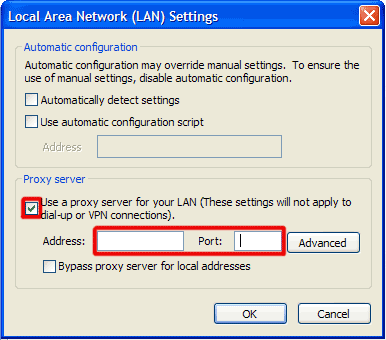
How to renew your internet connection:This rogue antispyware blocks your Internet connection to prevent you from removing the rogue application. To enable the Internet connection, please follow these instructions:
| ||||||||
|
Download Spyware Removal Tool to Remove*
Windows Ultimate Security Patch
| ||||||||

|
How to manually remove Windows Ultimate Security Patch
Files associated with Windows Ultimate Security Patch infection:
%CommonStartMenu%\Programs\Windows Ultimate Security Patch.lnk
%AppData%\1st$0l3th1s.cnf
%AppData%\result.db
%AppData%\Protector-[Random].exe
%AppData%\NPSWF32.dll
Windows Ultimate Security Patch DLL's to remove:
Windows Ultimate Security Patch processes to kill:
Remove Windows Ultimate Security Patch registry entries:
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings "WarnOnHTTPSToHTTPRedirect" = 0
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\System "DisableRegedit" = 0
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\System "DisableRegistryTools" = 0
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\System "DisableTaskMgr" = 0
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run "Inspector"
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Settings "net" = "2012-5-28_4"
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Settings "UID" = "mlfcdpliqw"
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\aAvgApi.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\bd_professional.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\fsav.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\mpftray.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\powerscan.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\soap.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\vscenu6.02d30.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\system "ConsentPromptBehaviorAdmin" = 0
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\system "ConsentPromptBehaviorUser" = 0
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\system "EnableLUA" = 0

Post comment — WE NEED YOUR OPINION!